The Ethical Dilemma of Public Vulnerability Disclosure: Balancing Security and Reputation in Tech
- Ctrl Man
- Technology , Cybersecurity , Ethics
- 19 Oct, 2024
The Ethical Dilemma of Publicly Highlighting Vulnerabilities in Software Projects: A Case Study of Twitter Disclosure
In the age of social media, developers have embraced a new culture of sharing their findings, including software vulnerabilities, on platforms like X/Twitter. This practice raises significant questions about ethical responsibility, security, and reputation management. Let’s explore these issues through a case study involving a coder who humorously pointed out a critical vulnerability in a widely used project on X/Twitter.
Understanding the Security Flaw
The coder identified a username validation flaw in the project that could lead to various injection vulnerabilities. The core issue lay in improper input validation, allowing special characters and excessively long strings for usernames. Such flaws could expose the application to SQL injection or cross-site scripting (XSS) attacks. Compounding the problem was the inconsistency between frontend and backend validation—UI restrictions were stricter than what the backend API accepted.
The potential consequences were significant: without proper server-side validation, malicious users could bypass security, and invalid data might compromise application integrity. While publishing a vulnerability on social media might generate buzz and demonstrate expertise, it also brings serious risks, especially when security flaws are publicly exposed before they’re fixed.
The Public Disclosure Dilemma on Social Media
Publicly disclosing vulnerabilities on platforms like Twitter can be tempting, offering quick visibility and engagement. In the case of “Ship.Fast,” a playful comment that the creator “@marc_louvion was shipping too fast” poked fun at missing server-side validation, but the tweet also exposed a critical issue to the world. While humorous in tone, such public disclosures can have unintended consequences.
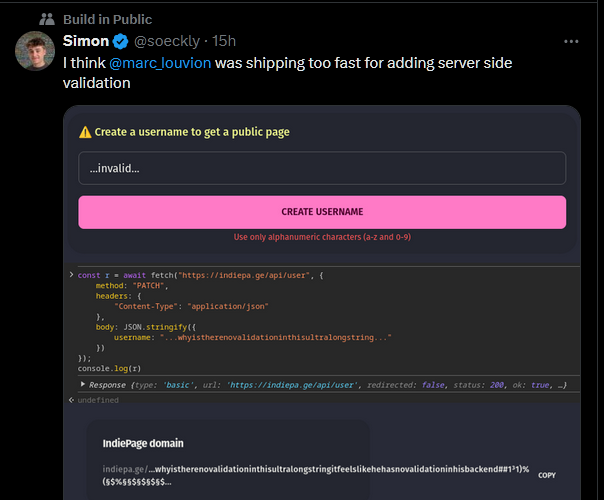
- Ethical Concerns: Exposing vulnerabilities without prior notice can leave users at risk before a fix is available.
- Reputational Damage: Publicly shaming developers or companies for bugs, even in a humorous way, can harm their reputation, especially for smaller projects with limited resources.
- Encouraging Malicious Activity: Disclosing security flaws publicly without remediation invites bad actors to exploit them.
- Legal Implications: Public disclosures can have legal ramifications, particularly if they result in harm to users or systems. Some jurisdictions may consider this an offense if responsible disclosure protocols aren’t followed.
A Real-World Example of Responsible Disclosure
Let’s contrast the Twitter scenario with a responsible disclosure success story from Marc Louvion’s own experience. Louvion tweeted about a security researcher, Jonas Scholz, who privately reported security vulnerabilities on his DataFast platform:
“He hacked my site… So I paid him $300.
@JonasScholz19 emailed me yesterday about potential security issues on DataFast.
– He didn’t ask anything
– He didn’t post it publicly
– It was legitSo I sent him $300*.
We are a small community of ambitious people trying to never work for a boss again while working on projects we love.
We aren’t perfect, we ship bugs sometimes.
Help each other out:
– Praise in public
– Roast in private(and keep shipping)”
In this case, Jonas adhered to responsible disclosure practices, reporting the issue privately, without seeking immediate recognition or reward. As a result, Marc was able to address the security flaw without reputational damage or legal risk, and he even rewarded Jonas for his professionalism. This story showcases the benefits of private, responsible reporting and fosters a culture of mutual respect and support.
- While the $300 payment to the researcher was a good-willed gesture, it does raise the question of adequate compensation for serious vulnerabilities. Given that many developers and tech solopreneurs can earn significant monthly revenues—such as Marc Louvion reportedly earning $60k-80k** monthly—there is a growing expectation that bug bounty programs should offer more attractive rewards, proportionate to the potential risk or damage a vulnerability could cause. Offering more generous compensation would not only incentivize ethical reporting but also reinforce the value of securing one’s platform. This is where structured bug bounty programs come in, helping to standardize compensation based on vulnerability severity.
Responsible Disclosure Practices
Responsible disclosure is the process of reporting security vulnerabilities privately to the developer or organization, giving them time to fix the issue before publicizing it. Here’s how to handle vulnerabilities responsibly:
- Contact the Developer Privately: Use direct channels such as email, DM, or official bug reporting platforms.
- Provide Clear Reproduction Steps: Detail the issue thoroughly, including steps to reproduce and its potential impact.
- Agree on a Timeline: Collaborate with the developer or organization on a reasonable timeline for fixing the issue before disclosing publicly.
- Use Recognized Channels for Public Disclosure: If no response is received, or if the issue isn’t fixed in a reasonable time, consider responsible public disclosure through trusted security platforms (e.g., CERT, HackerOne).
Legal and Ethical Implications
Failing to follow responsible disclosure processes can lead to legal consequences. In some countries, public disclosure of vulnerabilities without permission may violate cybersecurity laws. For instance, the U.S. Computer Fraud and Abuse Act (CFAA) could classify such actions as unauthorized access to computer systems.
Moreover, publicizing a vulnerability before a patch is available could expose users and organizations to unnecessary risk. For businesses, this could lead to financial losses, reputational damage, and loss of customer trust.
On the flip side, discoverers of vulnerabilities may feel pressure to publish flaws publicly if they believe companies are ignoring or downplaying the risks. However, ethical and legal frameworks suggest that private, responsible disclosure is the most effective way to balance user safety and organizational security.
The Role of Bug Bounty Programs
Bug bounty programs have emerged as a structured way for companies to encourage responsible disclosure. By offering financial rewards and public recognition, these programs incentivize ethical hackers to report vulnerabilities rather than exploit them. Platforms like HackerOne and Bugcrowd help bridge the gap between security researchers and companies, offering a safe space for vulnerability reporting while fostering collaboration.
For developers, embracing a bug bounty program can improve security, build trust with the community, and prevent the negative consequences of public disclosures. For discoverers, these programs provide a formalized, ethical path to report vulnerabilities and potentially earn a reward.
Balancing Marketing and Technical Expertise in Solopreneurship
In the tech world, especially among solopreneurs, marketing skills often eclipse pure coding talent. Developers like Marc Louvion, who excel at marketing, tend to succeed more visibly. While coders may envy the success of marketers, it’s important to recognize that both technical and non-technical skills play a role in building a successful business.
Successful solopreneurs blend coding expertise with storytelling, audience engagement, and product marketing. Coders can enhance their success by learning marketing basics or partnering with marketers who complement their skills.
Conclusion
In an open-source-driven tech ecosystem, promoting responsible problem-solving over public shaming is essential. Social media can be a powerful platform for visibility, but developers must exercise caution when dealing with sensitive security issues. Ethical vulnerability reporting protects users, preserves reputations, and fosters a more secure and collaborative tech community.
Engage with Responsibility
By adopting responsible disclosure practices, developers can contribute to a safer, more supportive tech ecosystem. Promoting ethical vulnerability reporting and collaboration, we can ensure that the tech landscape remains robust, secure, and conducive to open innovation.